Nekaj vtičnikov za zaščito, ki jih lahko uporabite za vaš CMS WordPress, za linux OS katerikoli Debian/Ubuntu/Fedora/CentOS,… priporočam Fail2Ban ali NinjaFirewall (Fail2Ban extra parametri požarni zid si prenesete lahko preko URL: https://perc.ddns.net/ddl/)
- Fail2Ban, če uporabljate linux server best off
- NinjaFirewall, če uporabljate linux server best off
- JetPack, katerakoli varianta serverja linux/windows
- AIOS, Vse v Enem Zaščita vtičnik vse različice strežnika
- Wordfence, Security – Firewall, Malware Scan, and Login Security wpZaščita Vsi operacijski sistemi
- Defender, Security – Malware Scanner, Login Security & Firewall wpZaščita Vsi operacijski sistemi
Preko tega URL objavljam redno slabi IP naslovi oz. BADIPs izključno za CMS Wordrpess:
https://perc.ddns.net/iplist-cms.txt
za Maltrail lahko vključite spodnje URL:
https://perc.ddns.net/iplist.txt
ALI POLNA KUMULATIVNA LISTA
https://perc.ddns.net/iplist-pcsnet.txt
DDL Javna mapa prenos dodatkov
Terminal komanda modul ipset za iptables požarni zid linux:
(če niste namestitli požarni zid za linux server, lahko izvedete spodnjo namestitev in zaščito strežnika preko iptable&fail2ban) Pripravite si v naprej vse vaše interne ip strežnikov in računalnikov za full dostop 192.168.0.1 npr. je router in server na 192.168.0.11 itd. ostalo.
# Prvo namesti iptables
sudo apt install iptables
sudo reboot
# Drugo pripravi požarni zid za svoj strežnik
sudo nano /tmp/v4
*mangle
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
*raw
:PREROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
-A INPUT -i lo -j ACCEPT
-A INPUT ! -i lo -d 127.0.0.0/8 -j REJECT
-A INPUT -d 127.0.0.0/8 -j REJECT --reject-with icmp-port-unreachable
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT ! -i eth0 -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags ACK ACK -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 80 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 443 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 21 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 25 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 143 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 993 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 110 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 995 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 8338 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 10000 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 11211 -j ACCEPT
-A INPUT -p tcp -m tcp -m multiport --dports 21,80,443,25,110,143,587,993,995,8338,10000,11211 -j ACCEPT
-A INPUT -i wlan0 -j ACCEPT
-A INPUT -i eth0 -j ACCEPT
-A INPUT -p tcp -m state --state NEW --dport 22 -j ACCEPT
-A INPUT -s 192.168.1.1/24 -p tcp -m state --state NEW,RELATED,ESTABLISHED -m tcp --dport 22 -j ACCEPT
-A INPUT -s 192.168.0.1/24 -p tcp -m state --state NEW,RELATED,ESTABLISHED -m tcp --dport 22 -j ACCEPT
-A INPUT -s 192.168.2.1/24 -p tcp -m state --state NEW,RELATED,ESTABLISHED -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m state --state NEW,RELATED,ESTABLISHED -m tcp --dport 22 -j DROP
-A INPUT -p tcp -m tcp --dport 21 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 25 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 80 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 110 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 143 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 443 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 465 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 587 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 993 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 995 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 4000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8442 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8338 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 10000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 11211 -j ACCEPT
-A INPUT -p udp -m state --state NEW,ESTABLISHED -m udp --dport 53 -j ACCEPT
-A INPUT -p udp -m udp --sport 8442 --dport 1024:65535 -j ACCEPT
-A INPUT -p udp -m udp --sport 8442 -j ACCEPT
-A INPUT -p udp -m udp --sport 53 -j ACCEPT
-A INPUT -s 192.168.1.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -s 192.168.0.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -s 192.168.1.133/32 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -s 192.168.1.87/32 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -i eth0 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -i wlan0 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 3306 -j ACCEPT
-A INPUT -s 192.168.1.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 5432 -j ACCEPT
-A INPUT -s 192.168.0.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 5432 -j ACCEPT
-A INPUT -i eth0 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 5432 -j ACCEPT
-A INPUT -i wlan0 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 5432 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 3142 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 22 -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -s 192.168.1.1/24 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -s 192.168.0.1/24 -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j DROP
-A INPUT -p tcp -m state --state NEW -m recent --set --name ssh --mask 255.255.255.255 --rsource -m tcp --dport 22
-A INPUT -p tcp -m state --state NEW -m recent ! --rcheck --seconds 120 --hitcount 6 --name ssh --mask 255.255.255.255 --rsource -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp --dport 80 -m limit --limit 20/minute --limit-burst 100 -j ACCEPT
-A INPUT -s 192.168.1.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 873 -j ACCEPT
-A INPUT -s 192.168.0.1/24 -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 873 -j ACCEPT
-A INPUT -p udp -m state --state NEW -m udp --dport 8442 -j ACCEPT
-A INPUT -p udp -m state --state NEW -m udp --dport 53 -j ACCEPT
-A INPUT -p udp -m state --state NEW -m udp --dport 5353 -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 113 -j ACCEPT
-A INPUT -m state --state NEW -p udp --dport 123 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 2049:2050 -j DROP
-A INPUT -p tcp -m tcp --dport 6000:6063 -j DROP
-A INPUT -p tcp -m tcp --dport 7000:7010 -j DROP
-A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables denied: " --log-level 7
-A INPUT -m conntrack --ctstate INVALID -j DROP
-A INPUT -j REJECT --reject-with icmp-port-unreachable
-A INPUT -j DROP
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m state --state INVALID -j DROP
-A FORWARD -j REJECT
-A FORWARD -j DROP
-A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i eth0 -o wlan0 -j ACCEPT
-A FORWARD -i eth0 -o wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i wlan0 -o eth0 -j ACCEPT
-A FORWARD -i eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i wlan0 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -p udp -m udp --dport 8442 -j ACCEPT
-A OUTPUT -d 8.8.8.8/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -d 8.8.4.4/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -d 9.9.9.9/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -d 149.112.112.112/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -d 208.67.222.222/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -d 208.67.220.220/32 -p udp -m udp --dport 53 -j ACCEPT
-A OUTPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT
-A OUTPUT -j ACCEPT
-A OUTPUT -p udp -m udp -m multiport --dports 123 -m state --state NEW -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 80 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 443 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 21 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 25 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 143 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 993 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 110 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 995 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 3306 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 4000 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 8442 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 8338 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 10000 -j ACCEPT
-A OUTPUT -o eth0 -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 3306 -j ACCEPT
-A OUTPUT -o wlan0 -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 3306 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 5432 -j ACCEPT
-A OUTPUT -o eth0 -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 5432 -j ACCEPT
-A OUTPUT -o wlan0 -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 5432 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 22 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --dport 22 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED -m tcp --sport 873 -j ACCEPT
-A OUTPUT -p tcp -m conntrack --ctstate NEW,ESTABLISHED -m tcp --sport 11211 -j ACCEPT
-A OUTPUT -d 192.168.1.1/24 -j ACCEPT
-A OUTPUT -d 192.168.0.1/24 -j ACCEPT
-A OUTPUT -d 192.168.1.133/32 -j ACCEPT
-A OUTPUT -d 192.168.1.66/32 -j ACCEPT
-A OUTPUT -d 192.168.1.68/32 -j ACCEPT
-A OUTPUT -d 192.168.1.113/32 -j ACCEPT
-A OUTPUT -d 192.168.1.254/32 -j ACCEPT
-A OUTPUT -d 192.168.1.87/32 -j ACCEPT
-A OUTPUT -p tcp -s 192.168.1.1/24 --dport 22 -j ACCEPT
-A OUTPUT -p tcp -s 192.168.0.1/24 --dport 22 -j ACCEPT
-A OUTPUT -p tcp --dport 22 -j DROP
-N block-scan
-A block-scan -p tcp --tcp-flags SYN,ACK,FIN,RST RST -m limit --limit 1/s -j RETURN
-A block-scan -j DROP
COMMIT
Shrani in exit
sudo nano /tmp/v6
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
*mangle
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
*raw
:PREROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
*filter
:FORWARD ACCEPT [0:0]
:INPUT DROP [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -i lo -j ACCEPT
# Dissalow input - connections from outsite localhost
-A INPUT -s ::1/128 ! -i lo -j REJECT
# Accept traffic from internal interfaces
-A INPUT ! -i eth0 -j ACCEPT
-A INPUT ! -i wlan0 -j ACCEPT
# Accept traffic with the ACK flag set
-A INPUT -p tcp -m tcp --tcp-flags ACK ACK -j ACCEPT
# Allow incoming data that is part of a connection we established
-A INPUT -m state --state ESTABLISHED -j ACCEPT
# Allow data that is related to existing connections
-A INPUT -m state --state RELATED -j ACCEPT
# Accept responses to DNS queries UPD connedtion port ipv4 8442 open all ports from 1024 to 65535
-A INPUT -p udp -m udp --dport 1024:65535 --sport 8442 -j ACCEPT
-A INPUT -p udp -m udp --dport 1024:65535 --sport 53 -j ACCEPT
-A INPUT -p tcp -m tcp -m multiport -j ACCEPT --dports ftp,www,https,pop3,smtp,imap,imaps,pop3s,123,8442,8338,10000,11211
## Allow connections to our IDENT server
-A INPUT -p tcp -m tcp --dport auth -j ACCEPT
# Respond to pings -A INPUT -p icmp -m icmp --icmp-type echo-request -j ACCEPT
## Protect our NFS server
-A INPUT -p tcp -m tcp --dport 2049:2050 -j DROP
# Protect our X11 display server
-A INPUT -p tcp -m tcp --dport 6000:6063 -j DROP
# Protect our X font server
-A INPUT -p tcp -m tcp --dport 7000:7010 -j DROP
-A INPUT -j REJECT
-A OUTPUT -j ACCEPT
-A FORWARD -i eth0 -o wlan0 -j ACCEPT
-A FORWARD -i wlan0 -o eth0 -j ACCEPT
-A FORWARD -j REJECT
COMMIT
# Shrani in izhod ter prikliči obe konfiguracije ter namesti iptalbes persistent vsi odgovori DA oz. YES
## prikliči nastavitve in instaliraj modul iptablas autostart:
sudo iptables-restore < /tmp/v4
sudo ip6tables-restore < /tmp/v6
## namesti modul iptables persistant ter požarni zid fail2ban:
sudo apt install iptables ipset iptables-persistent fail2ban -y
Vsi odgovori Da in ko se namesti reboot oz. ponovni zagon
sudo reboot
# Preveri če dela:
sudo iptables -L
sudo ip6tables -L
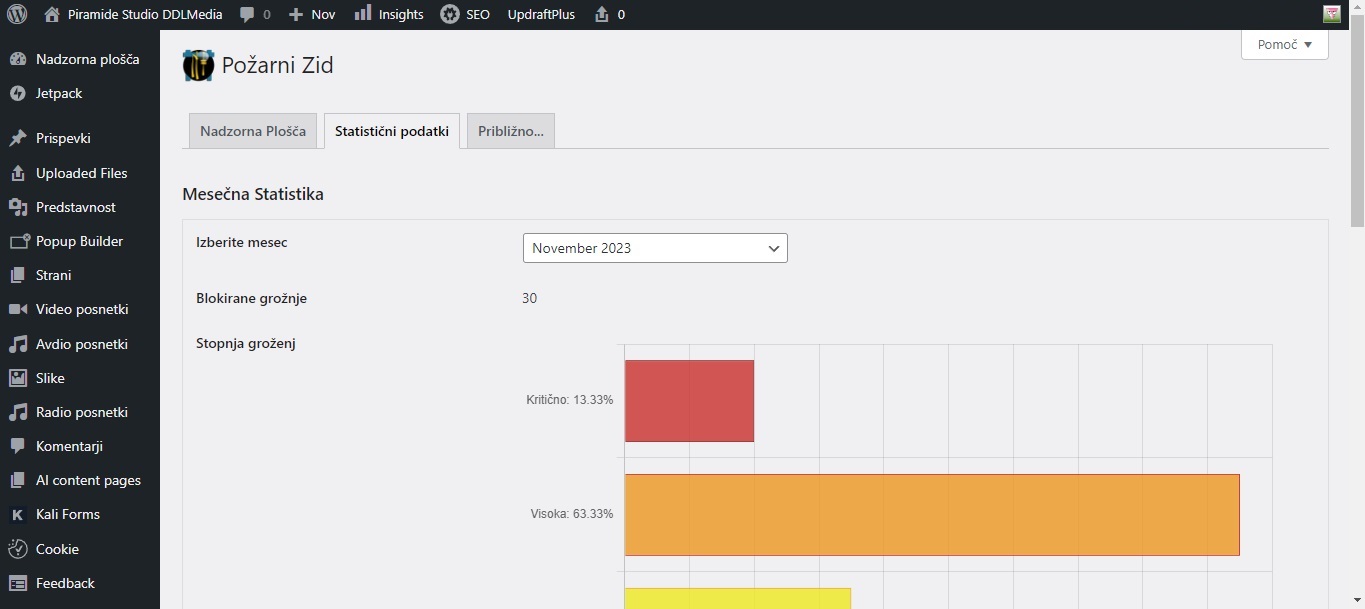
# Fail2Ban nastavitve:
sudo apt install fail2ban -y
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
sudo nano /etc/fail2ban/jail.local
enabled = true
filter = apache-badbots
ls /etc/fail2ban/filter.d/
Prenesite datoteko https://perc.ddns.net/ na vaš računalnik odpakirajte ter uredite filtre za aplikacije, katere uporabljate. DDLE filtri ne rabijo več, ker se je program lahko zaščiti z GoogleReCapt… Za wordpress lahko dodate prijavni filter, povečajte število neveljavnih prijav. Za Maltrail uporabite naš filter ali si napišite svoje parametre po želji, za integracijo slabih ip lahko uporabite;
BadIPs auto post:
https://perc.ddns.net/iplist-combined.txt
https://perc.ddns.net/iplist.txt
https://perc.ddns.net/iplist-pcsnet.txt
https://perc.ddns.net/iplist-cms.txt
https://perc.ddns.net/iplist-malware.txt
https://perc.ddns.net/iplist-server.txt
https://perc.ddns.net/iplist-world.txt
https://perc.ddns.net/iplist-ipsum.txt
https://perc.ddns.net/iplist-abuseip.txt
https://perc.ddns.net/iplist-blocklistde.txt
https://perc.ddns.net/iplist-sum.txt
https://perc.ddns.net/ip.blacklist
Za domače omrežje priporočam full lista https://pcsnet.mywire.org/iplist-pcsnet.txt za poslovno omrežje pa 95% lista najbolj aktivnih strežnikov, ki ne spoštuje direktiv vašega omrežja https://pcsnet.mywire.org/iplist.txt za CMS sisteme črna lista: https://piramide.zapto.org/iplist.txt ter ekstra za CMS WordPress črna lista https://perc.ddns.net/iplist-cms.txt
Shell skript blokada slabih omrežij
Ustvarite tri skripte in jim določite pooblastila 755
npr. v mapi /home/admin/scripts/sh/
sudo nano /home/admin/scripts/sh/perc-ips.sh
#!/bin/bash -l
ipset -q flush percip
##ipset -q create percip hash:net
ipset -q create percip hash:ip
for ip in $(curl https://perc.ddns.net/iplist.txt 2>/dev/null | grep -P '^[0-9.]+$'); do ipset add percip $ip; done
iptables -D INPUT -m set --match-set percip src -j DROP 2>/dev/null
iptables -I INPUT -m set --match-set percip src -j DROP
sudo chmod +x /home/admin/scripts/sh/perc-ips.sh
sudo nano /home/admin/scripts/sh/pcsnet-ips.sh
#!/bin/bash -l
ipset -q flush pcsnet
##ipset -q create pcsnet hash:net
ipset -q create pcsnet hash:ip
for ip in $(curl https://perc.ddns.net/iplist-pcsnet.txt 2>/dev/null | grep -P '^[0-9.]+$'); do ipset add pcsnet $ip; done
iptables -D INPUT -m set --match-set pcsnet src -j DROP 2>/dev/null
iptables -I INPUT -m set --match-set pcsnet src -j DROP
sudo chmod +x /home/admin/scripts/sh/pcsnet-ips.sh
sudo nano /home/admin/scripts/sh/ipsum.sh
#!/bin/bash -l
ipset -q flush ipsum
ipset -q create ipsum hash:ip
for ip in $(curl --compressed https://raw.githubusercontent.com/stamparm/ipsum/master/ipsum.txt 2>/dev/null | grep -v "#" | grep -v -E "\s[1-2]$" | cut -f 1); do ipset add ipsum $ip; done
iptables -D INPUT -m set --match-set ipsum src -j DROP 2>/dev/null
iptables -I INPUT -m set --match-set ipsum src -j DROP
sudo chmod +x /home/admin/scripts/sh/ipsum.sh
DODAJTE V KRONOLOŠKA OPRAVILA ENEGA OD ZGORNJIH SKRIPTOV:
/home/admin/scripts/sh/perc-ips.sh &>/dev/null 2>&1
ALI
/home/admin/scripts/sh/pcsnet-ips.sh &>/dev/null 2>&1
ter še zraven
/home/admin/scripts/sh/ipsum.sh &>/dev/null 2>&1
enkrat ali dvakrat dnevno po 3 zjutraj, se pravi 03:00, TXT datoteke osvežijo bazo podatkov od 00:00 do nekje 01:00 ure iz vseh različnih virov BinaryDefense, Kaspersky, BitDefender, AbuseIPDB, PCSNETNinjaFW (za CMS Drupal&Wordpress)
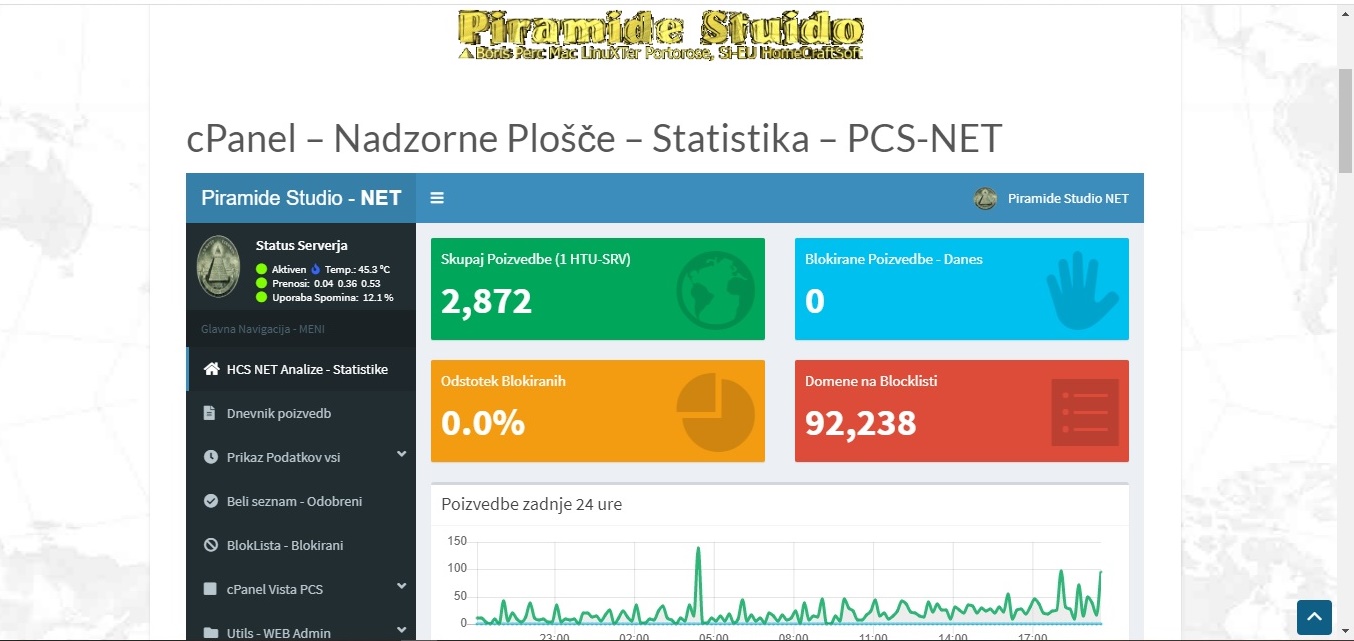
LIVE BLOCKED BADIPS FAIL2BAN MAILTRAIL SERVER https://pcsnet.mywire.org:3333/fail2ban
Živa lista Fail2Ban PCSNET, za integracijo v maltrail lahko uporabite v nastavitvah maltrail.conf
# Use remote custom feed (too) in trail updates
#CUSTOM_TRAILS_URL http://www.test.com/custom.txt
CUSTOM_TRAILS_URL https://perc.ddns.net/iplist.txt
lahko uporabite tudi to listo če uporabljate CMS Joomla, Drupal, WordPress kombinirano
CUSTOM_TRAILS_URL https://piramide.zapto.org/iplist-pcsnet.txt
Bloklista za AcrylicDNSProxy za privatno omrežje (blokada preko hosts komplet lista – NI NAMENJENO ZA POSLOVNA OMREŽJA) https://perc.ddns.net/ddl/hostspcsnet.zip