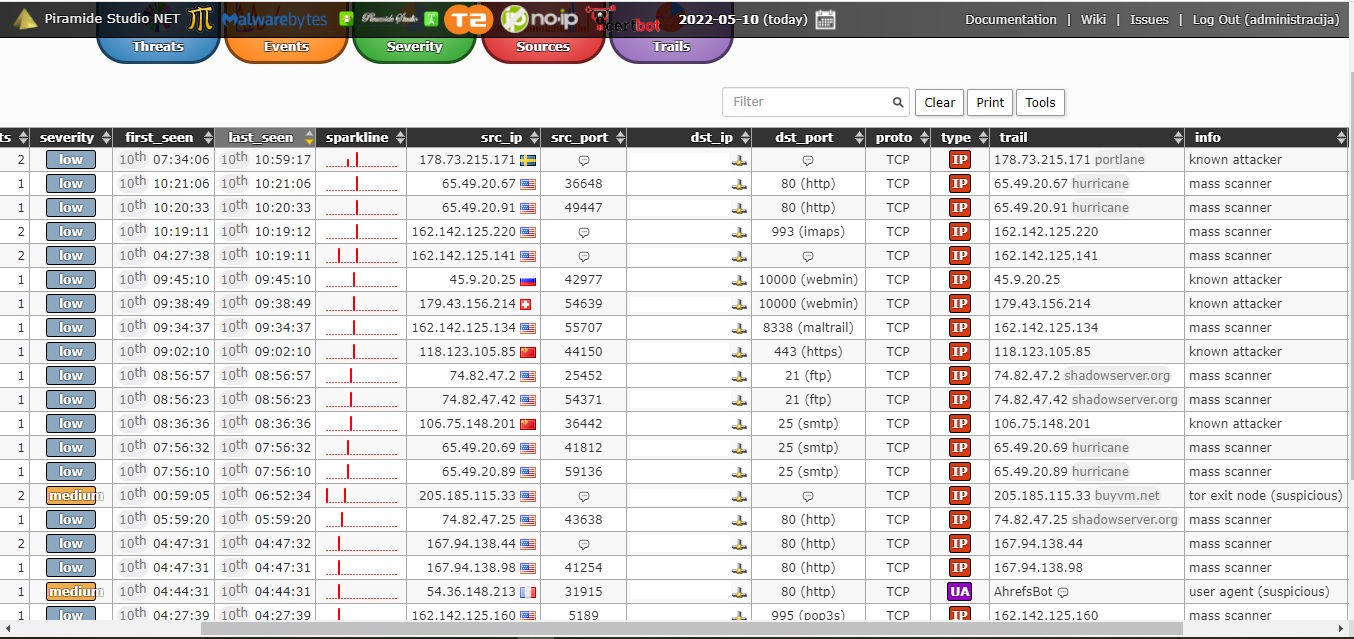
https://github.com/stamparm/maltrail
Najboljše prakse
- Install-Namestitev Maltrail:
-
Na Ubuntu/Debian
sudo apt-get install git python3 python3-dev python3-pip python-is-python3 libpcap-dev build-essential procps schedtool sudo pip3 install pcapy-ng cd /tmp git clone --depth 1 https://github.com/stamparm/maltrail.git sudo mv /tmp/maltrail /opt sudo chown -R $USER:$USER /opt/maltrail
-
Na SUSE/openSUSE
sudo zypper install gcc gcc-c++ git libpcap-devel python3-devel python3-pip procps schedtool sudo pip3 install pcapy-ng cd /tmp git clone --depth 1 https://github.com/stamparm/maltrail.git sudo mv /tmp/maltrail /opt sudo chown -R $USER:$USER /opt/maltrail
-
Nastavite delovno okolje:
sudo mkdir -p /var/log/maltrail sudo mkdir -p /etc/maltrail sudo cp /opt/maltrail/maltrail.conf /etc/maltrail sudo nano /etc/maltrail/maltrail.conf
-
Nastavite okolje za delovanje:
crontab -e # autostart server & periodic update
*/5 * * * * if [ -n "$(ps -ef | grep -v grep | grep 'server.py')" ]; then : ; else python3 /opt/maltrail/server.py -c /etc/maltrail/maltrail.conf; fi 0 1 * * * cd /opt/maltrail && git pullsudo crontab -e # autostart sensor & periodic restart
*/1 * * * * if [ -n "$(ps -ef | grep -v grep | grep 'sensor.py')" ]; then : ; else python3 /opt/maltrail/sensor.py -c /etc/maltrail/maltrail.conf; fi 2 1 * * * /usr/bin/pkill -f maltrail -
Omogoči kot storitve systemd (samo Linux):
sudo cp /opt/maltrail/maltrail-sensor.service /etc/systemd/system/maltrail-sensor.service sudo cp /opt/maltrail/maltrail-server.service /etc/systemd/system/maltrail-server.service sudo systemctl daemon-reload sudo systemctl start maltrail-server.service sudo systemctl start maltrail-sensor.service sudo systemctl enable maltrail-server.service sudo systemctl enable maltrail-sensor.service systemctl status maltrail-server.service && systemctl status maltrail-sensor.service
Note: /maltrail-sensor.service se lahko zažene kot namenska storitev brez vnaprejšnjega zagona /maltrail-server.service. To je uporabno za primer, ko /maltrail-server.service je nameščen in deluje na drugem računalniku v vašem omrežnem okolju.
License
This software is provided under a MIT License. See the accompanying LICENSE file for more information.
Sponsors
- Sansec (2020-2021)
Developers
- Miroslav Stampar (@stamparm)
- Mikhail Kasimov (@MikhailKasimov)
Zdaj ko imate nameščen Maltrail Senzor in Server za dodatno blokiranje Slabih IP lahko uporabite spodnji url ali si datoteko prenesete na vaš strežnik:
https://piramide.zapto.org/iplist.txt
V glavnih nastavitvah maltrail.conf poiščite Custom Trails URL in dodajte spodnje direktive:
# Use remote custom feed (too) in trail updates
CUSTOM_TRAILS_URL https://piramide.zapto.org/iplist-pcsnet.txt
Dve liste ki se nadgrajujeta enkrat dnevno vir Slabih IP naslovov KasperskyLAB, BitDefender, BinaryDefense, AbuseIP in Fail2Ban to omrežje:
https://pcsnet.mywire.org/iplist.txt – Živa lista Slaba omrežja (PCSNET BadIPS)
https://pcsnet.mywire.org/iplist-pcsnet.txt – Kumulativna lista Slaba omrežja (SecurityCompaniesReports)
Ne pozabit še cronjob za skript / (sudo apt install iptables ipset fail2ban):
#!/bin/bash
ipset -q flush maltrail
ipset -q create maltrail hash:net
for ip in $(curl http://127.0.0.1:8338/fail2ban 2>/dev/null | grep -P '^[0-9.]+$'); do ipset add maltrail $ip; done
iptables -I INPUT -m set --match-set maltrail src -j DROPDebian 11 / Ubuntu 20 CertBot SSL
sudo apt-get install -y git python3 python3-dev python3-pip libpcap-dev build-essential procps schedtool && sudo pip3 install pcapy-ng && sudo apt-get install git python3-pcapy -y
###SSL python
sudo apt-get install -y python3-openssl python3-openssl python-openssl-doc && sudo pip3 install pcapy-ng && sudo pip3 install pyopenssl
V glavnih nastavitvah maltrail.conf poiščite USE SSL in odkomintirajte kot je spodaj:
# Use SSL/TLS
USE_SSL true
# SSL/TLS (private/cert) PEM file (e.g. openssl req -new -x509 -keyout server.pem -out server.pem -days 1023 -nodes)
SSL_PEM misc/server.pem
Zdaj ker ste že aplicirali SSL CertBot kopirajte vaš ssl v server.pem:
sudo su
cd /opt/maltrail/misc
sudo cat /etc/letsencrypt/live/mojastran.si/cert.pem > server.pem
sudo cat /etc/letsencrypt/live/mojastran.si/privkey.pem > server.pem
sudo cat /etc/letsencrypt/live/mojastran.si/cert.pem >> server.pem
Lahko date npr. v cronjob oz. kronološka opravila kot root spodnje direktive enkrat mesečno:
sudo crontab -e
## Kopiraj na koncu:
@monthly cd /opt/maltrail/misc && sudo cat /etc/letsencrypt/live/mojastran.si/cert.pem > server.pem && sudo cat /etc/letsencrypt/live/mojastran.si/privkey.pem > server.pem
ali če ste dali v admin uporabniško mapo:
@monthly cd /home/admin/maltrail/misc && sudo cat /etc/letsencrypt/live/mojastran.si/cert.pem > server.pem && sudo cat /etc/letsencrypt/live/mojastran.si/privkey.pem > server.pem
Namestitev certbot:
sudo apt-get install certbot python3-certbot-apache -y
sudo apt update
sudo apt install snapd -y
sudo snap install core
sudo snap refresh core
sudo snap install --classic certbot
sudo ln -s /snap/bin/certbot /usr/bin/certbot
## Renovirat SSL
sudo certbot renew --dry-run
## Nov certifikat!!!
sudo certbot --apache
sudo apt-get install certbot python3-certbot-apache -y
sudo certbot --apache
sudo certbot --apache certonly
sudo certbot renew --dry-run